It appears that the NSA (“or someone”) hacked into the code of a popular firewall and planted a password in there that would allow them access as needed.
That means the NSA (“or someone”) would be able to bypass the security features of a network and do what they wanted inside. This is basically an act of sabotage. Given that American organizations as well as foreign ones use these same firewalls, and that the planted password could be discovered by others outside the NSA, the act made vulnerable a multitude of innocent, untargeted systems.
Juniper Networks makes a popular line of enterprise firewalls whose operating system is called Screen OS. The company raised alarm bells with an advisory announcing that they’d discovered “unauthorized code” in some versions of Screen OS, a strange occurrence that hinted that a security agency had managed to tamper with the product before it shipped. One possible route would be for any such agency to have its own people inside the company, acting under cover.
An investigator for Juniper reported that he and his team have confirmed that the “unauthorized code” is a backdoor whose secret password enables the wielder to telnet or ssh into Juniper’s appliances. The password is <<< %s(un=’%s’) = %u, “presumably chosen so that it would be mistaken for one of the many other debug format strings in the code.” Further investigation located 26,000 Juniper devices that are vulnerable to this attack until patched.
The code appears to have been in multiple versions of the company’s ScreenOS software going back to at least August 2012.
The next mystery to solve is where this unauthorized code comes from. In this case, someone deliberately inserted a backdoor password into Juniper’s devices. Juniper says the hack is sophisticated enough that it had to have been made by a state-level actor. This was not done by your movie-version basement hacker.
“The weakness in the VPN itself that enables passive decryption is only of benefit to a national surveillance regime like the British, the U.S., the Chinese, or the Israelis,” said one researcher at the International Computer Science Institute and UC Berkeley. “You need to have wiretaps on the Internet for that to be a valuable change to make in the software.”
That’s a huge deal.
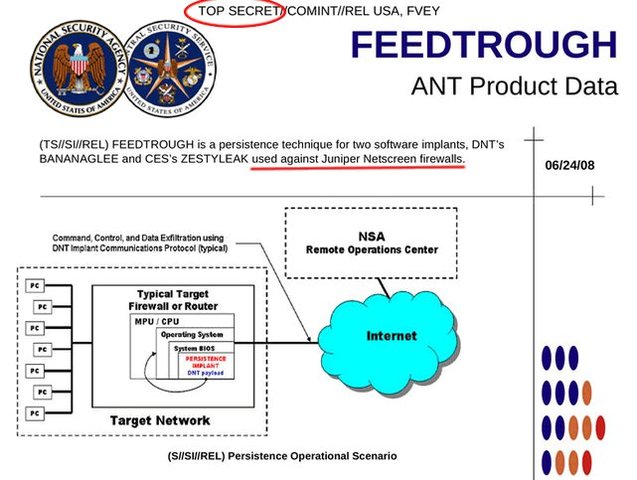
If it’s the NSA (which looks possible, given a Snowden leak about a program called FEEDTROUGH that installs persistent backdoors in Juniper devices) then it will mean that the U.S. government deliberately sabotaged tens, if not hundreds, of thousands of networks that were protected by products from a U.S. company that is the second-largest provider of networking equipment in the world (after Cisco.)
Or was the second-largest provider. Discovery of the backdoor is unlikely to be good for business.
Reprinted with permission from WeMeantWell.com.